Android 16 QPR1 is a big deal for #GrapheneOS.
All of the major desktop mode features will be available in this version. A lot of it is available as developer options for an early preview on GrapheneOS but will be fully production ready by the time we have A16 QPR1.
This will allow a Desktop experience for users. Modern Pixels can then dock their device and use a mouse and keyboard to navigate the UI.
 A functional desktop mode is huge, but it is a stepping stone towards a far greater feature target for us: A Desktop OS VM manager.
One OS feature (the Linux terminal app) already provides a Linux command line using a Debian virtual machine. Ideally, we would want to move away from a non-hardened desktop distribution like Debian, which the upstream uses, and have something an ARM build of secureblue, securecore or even a gold target for Windows 11 ARM for superior app compatibility.
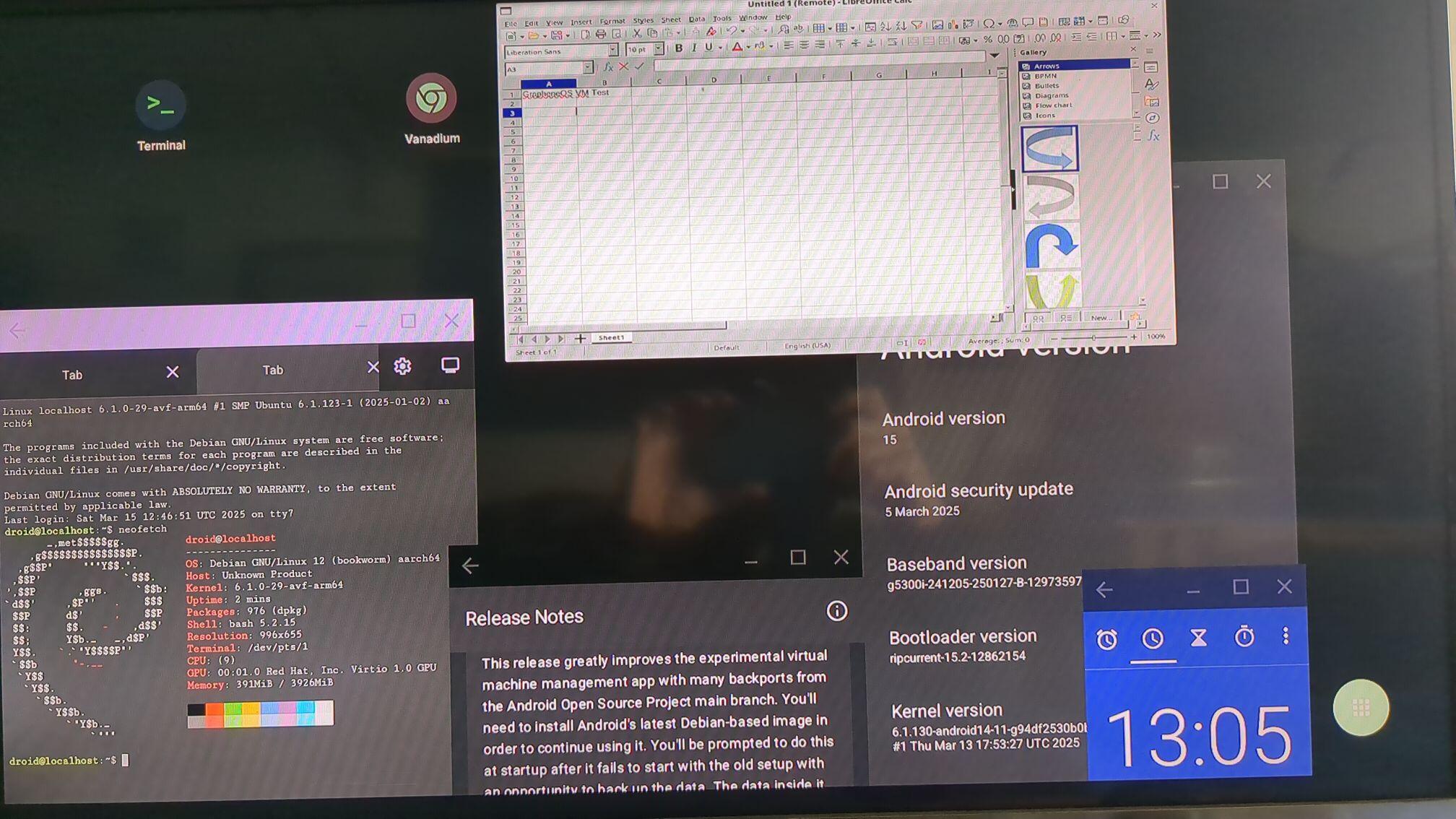
Here you can see desktop operating system apps within a freeform window over the standard GrapheneOS applications. There are many unique setups and software choices if we can further develop this:
View quoted note →
Gaining desktop functionality and including being able to run GUI Windows and desktop Linux applications via hardware accelerated virtualization will then lead to further innovative features, including:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
3) Create an amnesiac virtualized environment nested within the OS user that could be plausibly deniable.
There are also a few massive targets that would take a lot of work and wouldn't be seen yet, but worth considering. For example, Android provides Chromium's layer-1 sandbox as an OS feature available to be used by any app via isolatedProcess. It would be fantastic to move this to virtualization using microdroid. It'd be a large project, but have a very high impact for browsers, like per-site virtual machine instances. That would provide security above Tor Browser and comparable to Microsoft Edge's deprecated Application Guard feature that ran Edge in an isolated virtual machine but at a more seamless and useable scale.
Since isolatedProcess is an OS API, it'd benefit all Chromium-based browsers and other apps using it rather than being specific to Vanadium. That'd be a difficult project but we can consider it as a future large feature on the same scale as our sandboxed Google Play feature. This would make many apps get a large security boost.
A functional desktop mode is huge, but it is a stepping stone towards a far greater feature target for us: A Desktop OS VM manager.
One OS feature (the Linux terminal app) already provides a Linux command line using a Debian virtual machine. Ideally, we would want to move away from a non-hardened desktop distribution like Debian, which the upstream uses, and have something an ARM build of secureblue, securecore or even a gold target for Windows 11 ARM for superior app compatibility.
Here you can see desktop operating system apps within a freeform window over the standard GrapheneOS applications. There are many unique setups and software choices if we can further develop this:
View quoted note →
Gaining desktop functionality and including being able to run GUI Windows and desktop Linux applications via hardware accelerated virtualization will then lead to further innovative features, including:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
3) Create an amnesiac virtualized environment nested within the OS user that could be plausibly deniable.
There are also a few massive targets that would take a lot of work and wouldn't be seen yet, but worth considering. For example, Android provides Chromium's layer-1 sandbox as an OS feature available to be used by any app via isolatedProcess. It would be fantastic to move this to virtualization using microdroid. It'd be a large project, but have a very high impact for browsers, like per-site virtual machine instances. That would provide security above Tor Browser and comparable to Microsoft Edge's deprecated Application Guard feature that ran Edge in an isolated virtual machine but at a more seamless and useable scale.
Since isolatedProcess is an OS API, it'd benefit all Chromium-based browsers and other apps using it rather than being specific to Vanadium. That'd be a difficult project but we can consider it as a future large feature on the same scale as our sandboxed Google Play feature. This would make many apps get a large security boost.
 A functional desktop mode is huge, but it is a stepping stone towards a far greater feature target for us: A Desktop OS VM manager.
One OS feature (the Linux terminal app) already provides a Linux command line using a Debian virtual machine. Ideally, we would want to move away from a non-hardened desktop distribution like Debian, which the upstream uses, and have something an ARM build of secureblue, securecore or even a gold target for Windows 11 ARM for superior app compatibility.
Here you can see desktop operating system apps within a freeform window over the standard GrapheneOS applications. There are many unique setups and software choices if we can further develop this:
View quoted note →
Gaining desktop functionality and including being able to run GUI Windows and desktop Linux applications via hardware accelerated virtualization will then lead to further innovative features, including:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
3) Create an amnesiac virtualized environment nested within the OS user that could be plausibly deniable.
There are also a few massive targets that would take a lot of work and wouldn't be seen yet, but worth considering. For example, Android provides Chromium's layer-1 sandbox as an OS feature available to be used by any app via isolatedProcess. It would be fantastic to move this to virtualization using microdroid. It'd be a large project, but have a very high impact for browsers, like per-site virtual machine instances. That would provide security above Tor Browser and comparable to Microsoft Edge's deprecated Application Guard feature that ran Edge in an isolated virtual machine but at a more seamless and useable scale.
Since isolatedProcess is an OS API, it'd benefit all Chromium-based browsers and other apps using it rather than being specific to Vanadium. That'd be a difficult project but we can consider it as a future large feature on the same scale as our sandboxed Google Play feature. This would make many apps get a large security boost.
A functional desktop mode is huge, but it is a stepping stone towards a far greater feature target for us: A Desktop OS VM manager.
One OS feature (the Linux terminal app) already provides a Linux command line using a Debian virtual machine. Ideally, we would want to move away from a non-hardened desktop distribution like Debian, which the upstream uses, and have something an ARM build of secureblue, securecore or even a gold target for Windows 11 ARM for superior app compatibility.
Here you can see desktop operating system apps within a freeform window over the standard GrapheneOS applications. There are many unique setups and software choices if we can further develop this:
View quoted note →
Gaining desktop functionality and including being able to run GUI Windows and desktop Linux applications via hardware accelerated virtualization will then lead to further innovative features, including:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
3) Create an amnesiac virtualized environment nested within the OS user that could be plausibly deniable.
There are also a few massive targets that would take a lot of work and wouldn't be seen yet, but worth considering. For example, Android provides Chromium's layer-1 sandbox as an OS feature available to be used by any app via isolatedProcess. It would be fantastic to move this to virtualization using microdroid. It'd be a large project, but have a very high impact for browsers, like per-site virtual machine instances. That would provide security above Tor Browser and comparable to Microsoft Edge's deprecated Application Guard feature that ran Edge in an isolated virtual machine but at a more seamless and useable scale.
Since isolatedProcess is an OS API, it'd benefit all Chromium-based browsers and other apps using it rather than being specific to Vanadium. That'd be a difficult project but we can consider it as a future large feature on the same scale as our sandboxed Google Play feature. This would make many apps get a large security boost.LibreOffice Calc in #GrapheneOS Debian VM running on an external display in the launcher with 'freeform windows in external display' switched on:
View quoted note →
