With the development branch of #GrapheneOS, we've already successfully already tested Chrome running on top of Wayland with GPU acceleration working via ANGLE on the host. You'll be able to have a GPU accelerated virtual desktop OS that's usable via DisplayPort alternate mode.
Our 2025030900 release currently in the Beta channel is the first one with support for managing hardware-based virtual machines via the Terminal app in Android 15 QPR2. Since then, we've backported massive improvements to the feature for an upcoming new release, maybe even today.
Backports include terminal tabs, GUI support with opt-in GPU hardware acceleration (ANGLE-based VirGL until GPU virtualization support is available), speaker/microphone support and fixes for a bunch of bugs including overly aggressive timeouts. We're working on VPN compatibility.
At the moment, the Terminal app isn't compatible with having a VPN in the Owner user. It only works if VPN lockdown (leak blocking) is disabled and the VPN allows local traffic to pass through. It's also not clear how it SHOULD interact with a VPN since VPNs are profile-specific. #GrapheneOS
View quoted note →
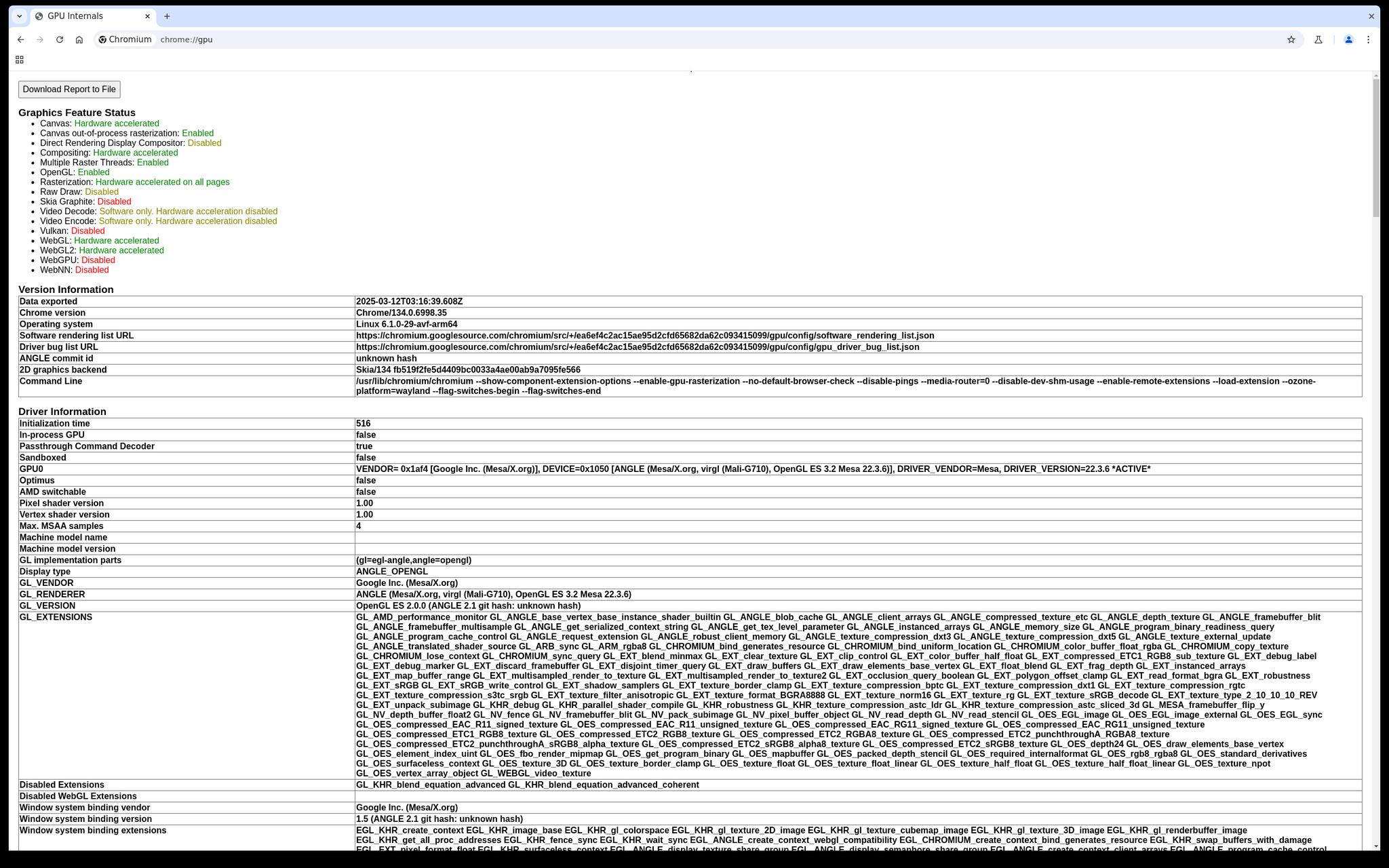 Our next release also enables running the Terminal app in secondary users. There's still the temporary limitation of only being able to use a single VM on the device at a time because the dedicated internal network interface it uses for the Terminal app isn't split up at all yet.
GUI VM support will have 2 main use cases:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
This virtual machine management app (Terminal) will be handling the 2nd case. It's essentially already available in a very primitive way. We expect this to become much more usable and robust entirely from the upstream Android work on the virtual machine and desktop mode features.
Our next release also enables running the Terminal app in secondary users. There's still the temporary limitation of only being able to use a single VM on the device at a time because the dedicated internal network interface it uses for the Terminal app isn't split up at all yet.
GUI VM support will have 2 main use cases:
1) Running a specific app or an entire profile via GrapheneOS virtual machines seamlessly integrated into the OS.
2) Running Windows or desktop Linux applications with desktop mode + USB-C DisplayPort alt mode on the Pixel 8 and later.
This virtual machine management app (Terminal) will be handling the 2nd case. It's essentially already available in a very primitive way. We expect this to become much more usable and robust entirely from the upstream Android work on the virtual machine and desktop mode features.

