I've implemented a BitStream proof of concept by Robin Linus in Cashu for atomic swaps between files and Lightning payments.
Atomicity is achieved via a "Nutbond" Ecash contract which can be challenged if the downloaded file doesn't decrypt right.
An explainer and demo video is linked below.
How it works:
- Clients requests download
- Server sends encrypted file, Lightning invoice & Nutbond
- Client verifies bond and pays LN invoice
- Client decrypts file with LN preimage
- If decrypt fails, client challenges Nutbond & gets refund
Some notable differences to the original proposal:
- Nutbonds are issued for each user, not per file
- Bond doesn't burn but acts as a refund to user
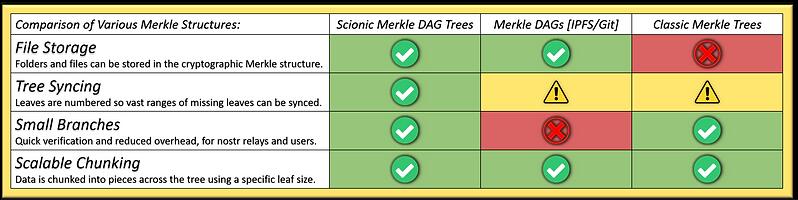
- No Merkle trees yet. Next logical step. Vibes well with BitTorrent.
- Bond is Ecash. Payment is on LN, could also be Ecash.
This took me a few hours to implement showing how easy it is to experiment with new contracting primitives in Cashu.
Bitcoiners are coming up with beautiful solutions for practical problems. Special thanks to Robin for sharing his cool ideas with us. Love the energy!
🎥👇 Demo (10 min):
 Original post:
Original post: 


82.07 MB file on MEGA

X (formerly Twitter)
яobin linus (@robin_linus) on X
BitStream: Decentralized File Hosting Incentiviced via Bitcoin Payments
https://t.co/cdVIqcC5Ec