#Amethyst Tricks
How to run a private relay over Tor on Android.
With the latest Amethyst supporting outbox & Tor this is more feasible than ever. Host one of your outbox relays on your phone, totally under your control.
🔹Citrine setup
Go to the settings tab. 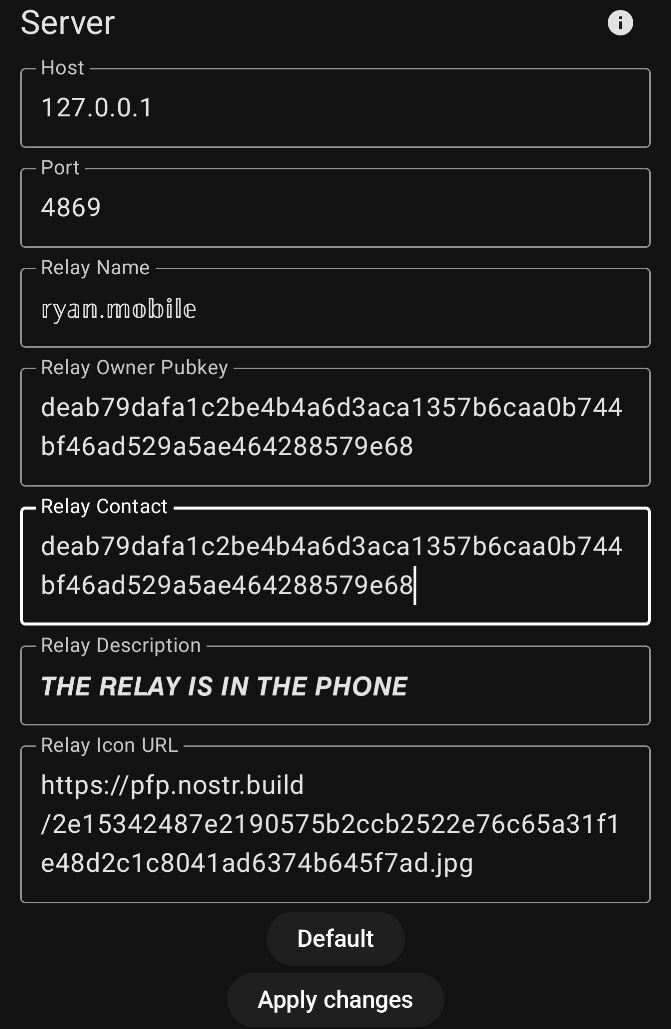 Fill things in as appropriate. Leave the network related settings default.
Fill things in as appropriate. Leave the network related settings default.
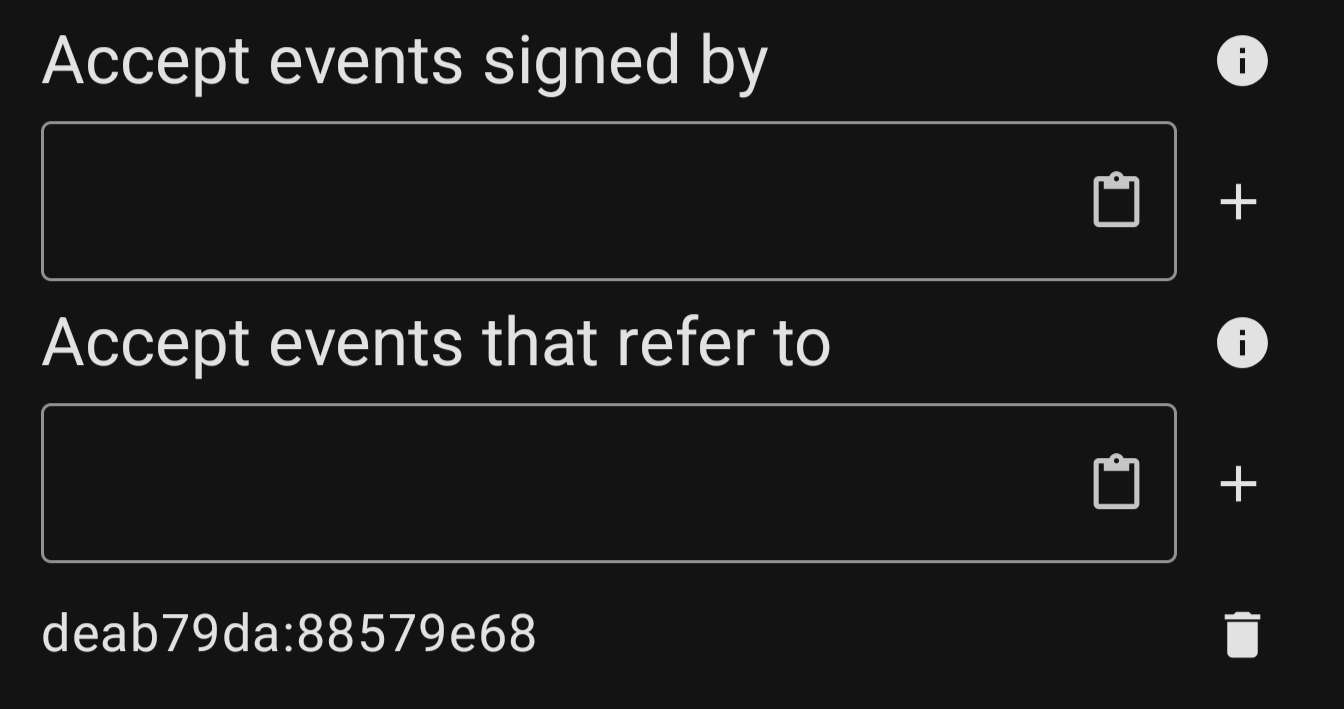 Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
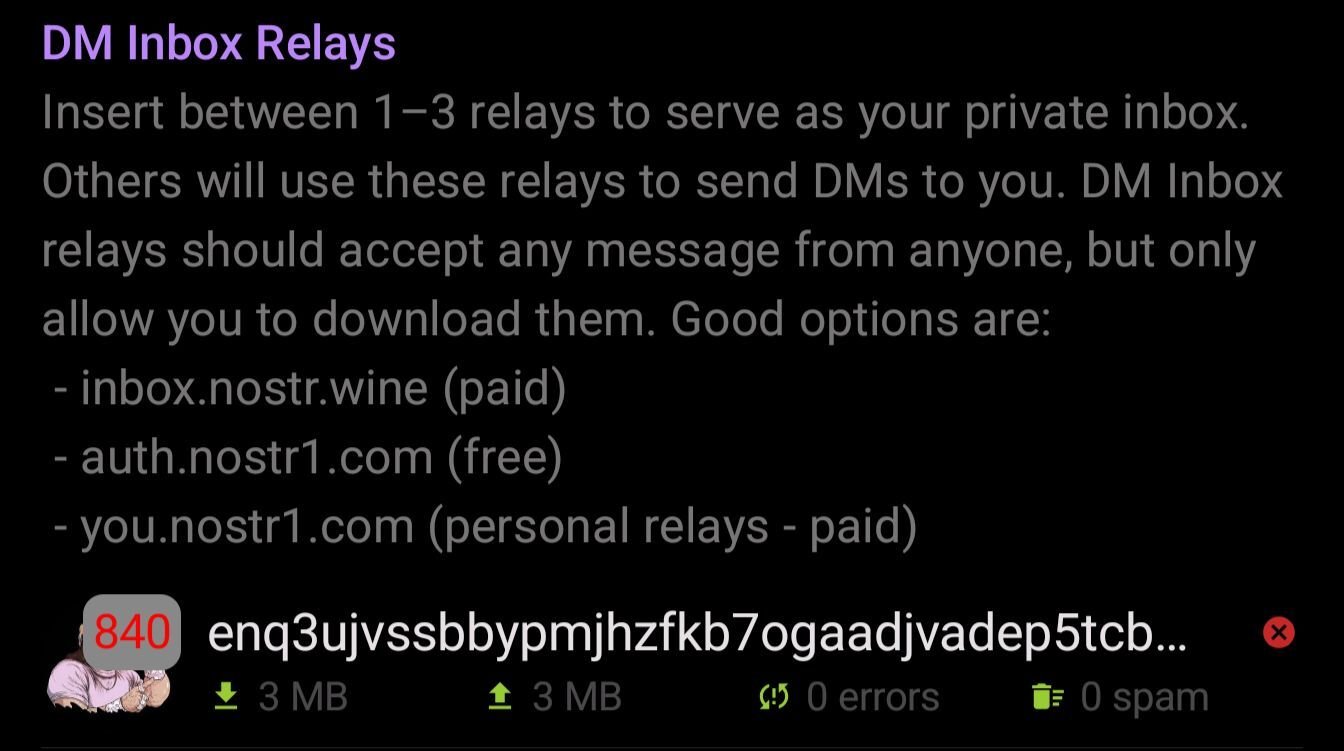 Also add ws://127.0.0.1:4869 as a local relay.
Also add ws://127.0.0.1:4869 as a local relay.
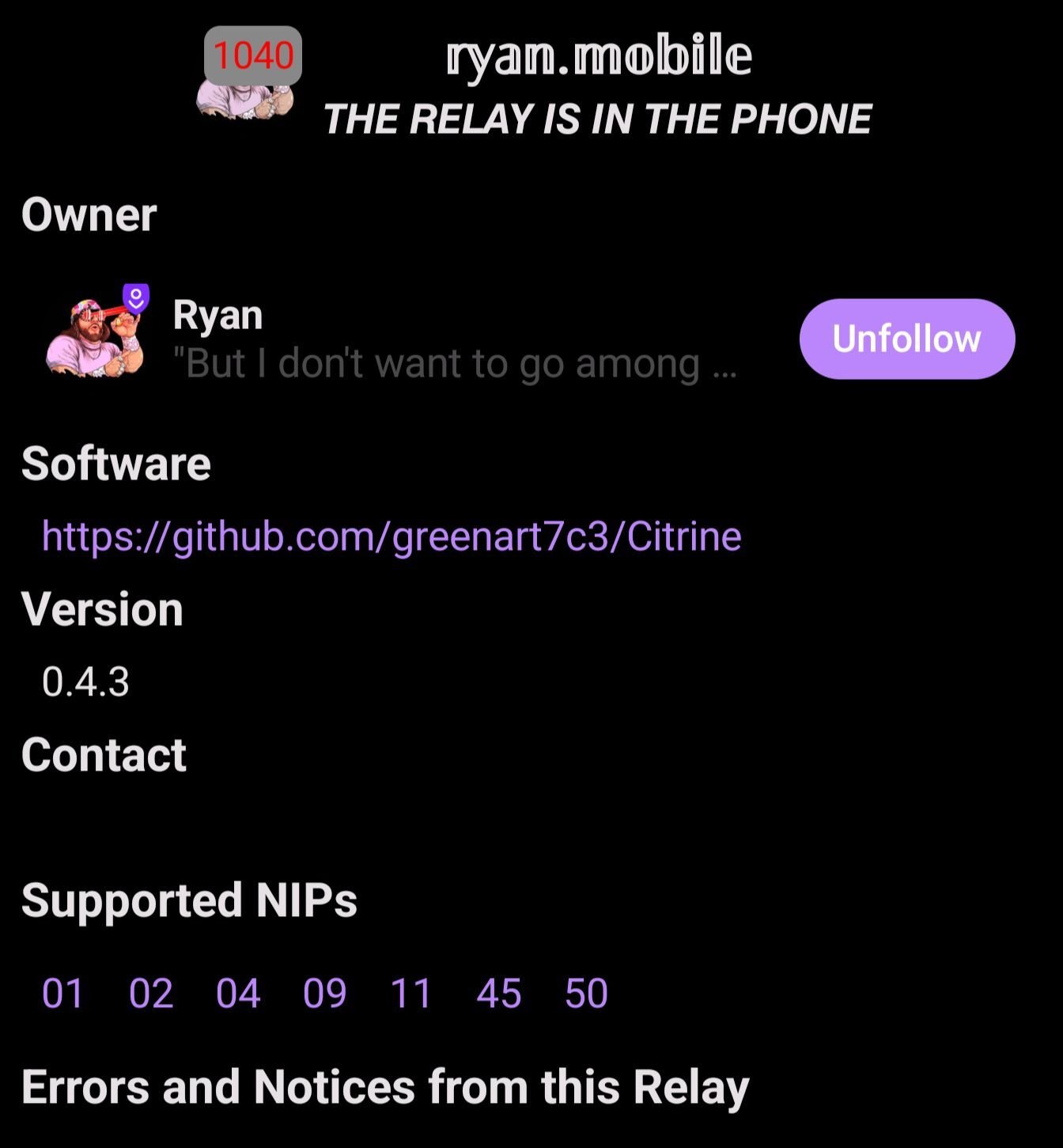
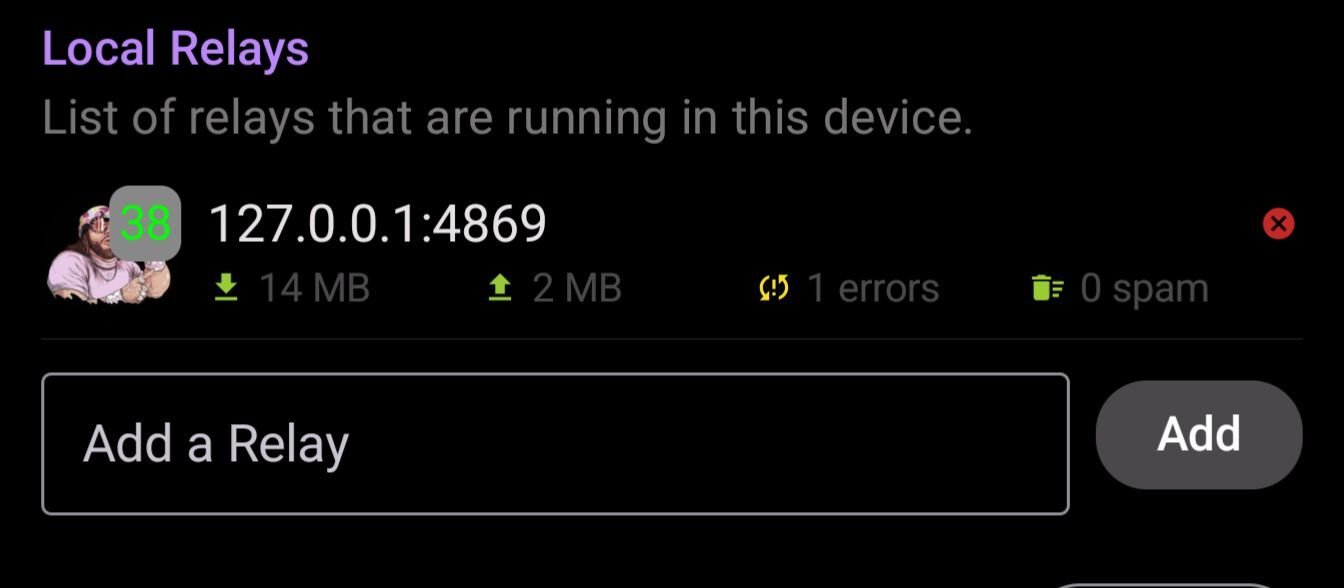 You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
 😎👌
Software required
😎👌
Software required



 Fill things in as appropriate. Leave the network related settings default.
Fill things in as appropriate. Leave the network related settings default.
 Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
 Also add ws://127.0.0.1:4869 as a local relay.
Also add ws://127.0.0.1:4869 as a local relay.
 You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
 😎👌
Software required
😎👌
Software required
GitHub
GitHub - vitorpamplona/amethyst: Nostr client for Android
Nostr client for Android. Contribute to vitorpamplona/amethyst development by creating an account on GitHub.
GitHub
GitHub - greenart7c3/Citrine: A Nostr relay in your phone
A Nostr relay in your phone. Contribute to greenart7c3/Citrine development by creating an account on GitHub.
GitHub
GitHub - guardianproject/orbot-android: The Github home of Orbot: Tor on Android (Also available on gitlab!)
The Github home of Orbot: Tor on Android (Also available on gitlab!) - guardianproject/orbot-android











