IBM Boosts Guardium Platform to Address Shadow AI, Quantum Cryptography
IBM is updating and upgrading its Guardium platform to provide security for the two primary new technology problems: AI models and quantum safety.
IBM Guardium AI Security and IBM Guardium Quantum Safe combine to form the newly launched IBM Guardium Data Security Center, which operates across the entire enterprise hybrid infrastructure
See more: 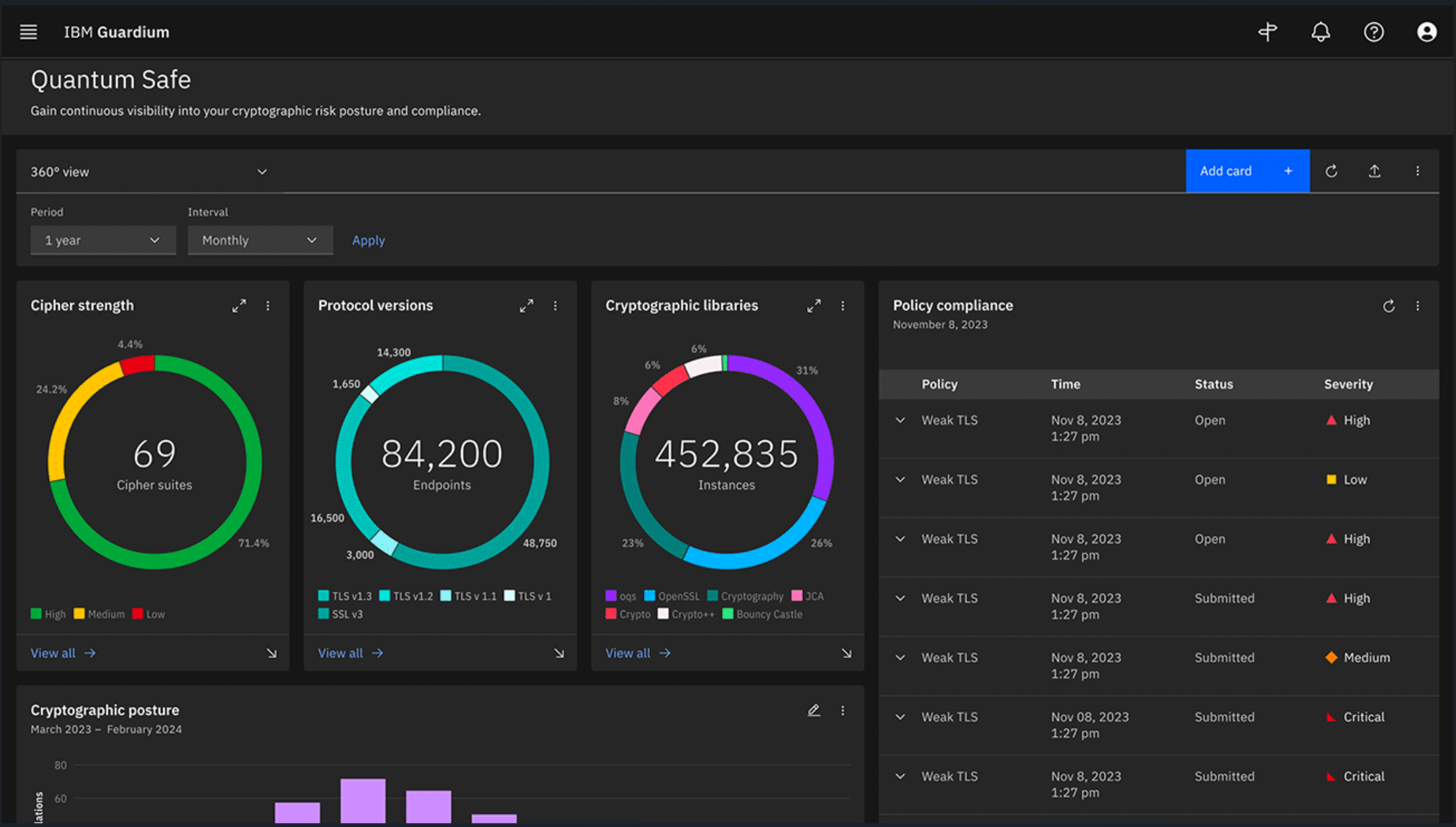 #cybersecurity
#cybersecurity

SecurityWeek
IBM Boosts Guardium Platform to Address Shadow AI, Quantum Cryptography
IBM announced updating and upgrading its Guardium platform to provide security for AI models and quantum safety.








