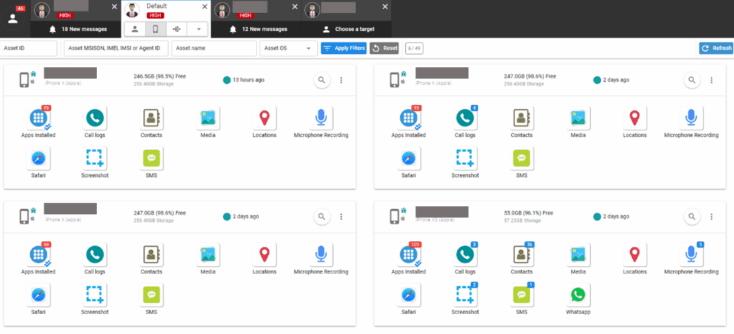
NEW: Staffers at notorious spyware maker Intellexa had live remote access to their customers' surveillance systems.
This allowed them to see the personal data of targets hacked with Intellexa's spyware Predator, according to new research based on a leaked training video.
Needless to say, this is bad for several reasons.

TechCrunch
Sanctioned spyware maker Intellexa had direct access to government espionage victims, researchers say | TechCrunch
Based on a leaked video, security researchers alleged that Intellexa staffers have remote live access to their customers' surveillance systems...









