Hackers took control of Qix’s npm account and published malicious versions in widely used npm packages containing a crypto-clipper to steal mainly from wallets and products that require making and signing transactions. More details at:
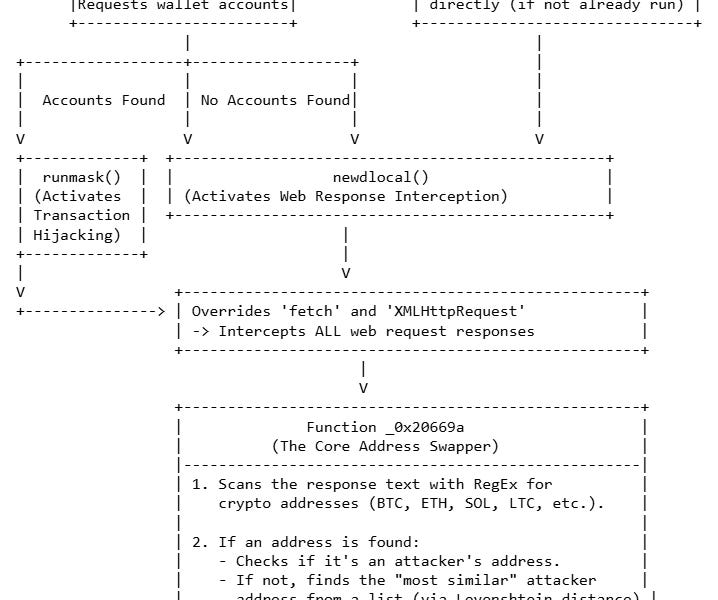
Anatomy of a Billion-Download NPM Supply-Chain Attack
A massive NPM supply chain attack has compromised foundational packages like Chalk, affecting over 1 billion weekly downloads. We dissect the crypt...
At least in the Bitcoin ecosystem I haven’t seen anything affected so far (wallets usually prefer not to use JavaScript/TypeScript, so very few depend on npm). I have seen wallets from other blockchains and products affected, as well as people who have already been robbed.
As a user it’s difficult to prevent this, but as developers we can. When developing in JavaScript/TypeScript, we should evaluate which libraries we add and whether they’re truly necessary, also review the libraries used within others (yes, this is common), and avoid updating without first checking what changed.



