At least some 300,000 machines reachable on the internet are vulnerable to a remote code execution vulnerability that appears to be rather easy to execute on all of those.
The vulnerable package is cups-browsed - a tool for printing - which does get installed by default on many desktop linux systems but who knows ... maybe you are running some media server with your bitcoin wallet and your printer reachable via the same RaspberryPi?
Check your machines. Android appears not to run cups but if you run Linux or Mac, you might want to double-check if you're one of the lucky 300,000 that get to update their system **now**.


evilsocket
Attacking UNIX Systems via CUPS, Part I

 With snapcraft obviously being tricky:
With snapcraft obviously being tricky:
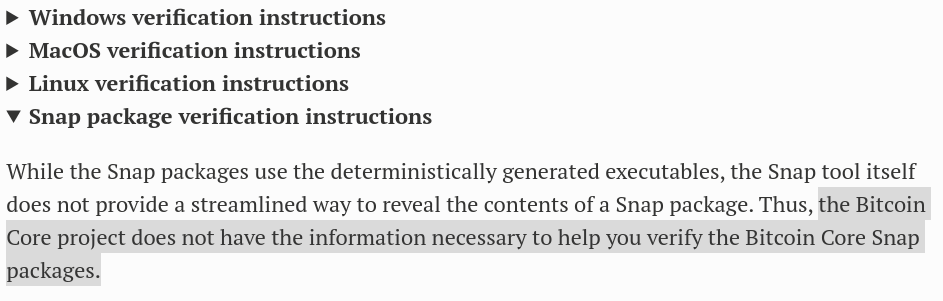 Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers.
Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers. But running these tests must have been great fun, right
But running these tests must have been great fun, right