 WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!
WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!WalletScrutiny

WalletScrutiny
npub1j9kt...uswx
Know your wallet like you made it!
Our goal is to improve the security of Bitcoin wallets by examining products for transparency and potential attacks.
 WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!
WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!We’ve been busy but quiet these last months. @npub1qw6s...4882 improved the site a lot by adding new features around #nostr based build verifications.
We hope other projects in the nostr ecosystem like @franzap @Zapstore will see the value of these verifications and start integrating them. The more products that build on reproducibility, the more users can truly apply the principle of “Don’t trust - verify.” Binary transparency shouldn’t remain a niche feature - it needs to become the default.
If you run software that touches your private keys - be it nostr clients or bitcoin wallets - without binary transparency, only whoever built the binary really knows what code you’re running.
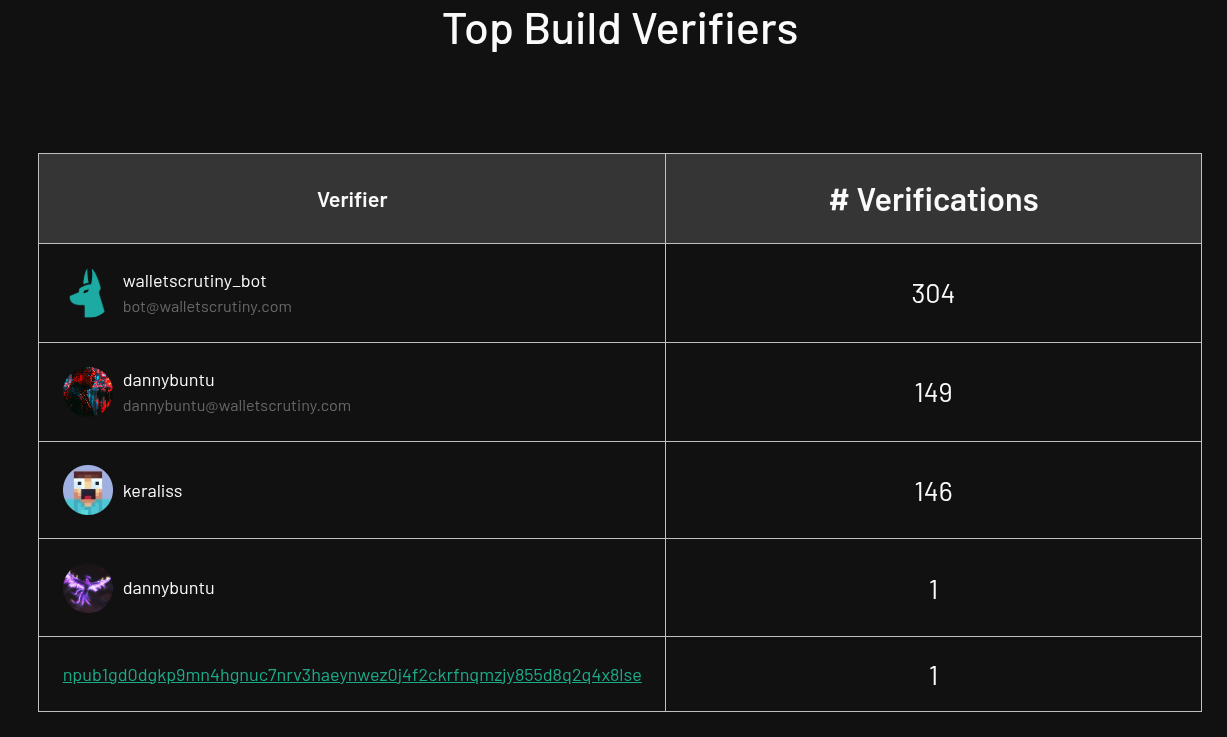 @npub1r709...sf7d and @npub1vf6w...t9ys checked the reproducibility of almost 300 binaries. The 304 verifications by @npub1z69h...aukf are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
@npub1r709...sf7d and @npub1vf6w...t9ys checked the reproducibility of almost 300 binaries. The 304 verifications by @npub1z69h...aukf are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
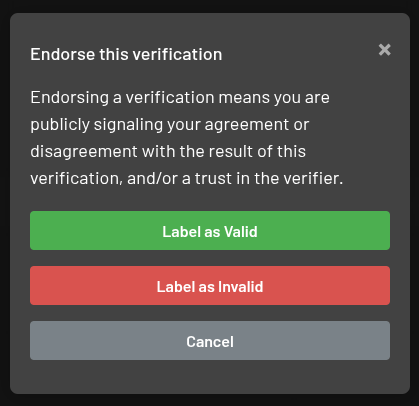 This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
 @npub1r709...sf7d and @npub1vf6w...t9ys checked the reproducibility of almost 300 binaries. The 304 verifications by @npub1z69h...aukf are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
@npub1r709...sf7d and @npub1vf6w...t9ys checked the reproducibility of almost 300 binaries. The 304 verifications by @npub1z69h...aukf are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
 This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!The ByBit Hack Report [1] reveals interesting details.
While many blame ETH and its complexities, it's important to note that a combination of circumstances made this attack possible.
But the core issue clearly was a central point of failure. Multi Signature was used but all signers used the same hacked, remote server.
The server was trusted, supposedly running a well audited open source web wallet software but "open source" is not enough as the source run on that compromised server did not match the well audited code.
At WalletScrutiny we so far do not list web wallets because it is hard if not impossible to attest to the integrity of web wallet code when the server can serve different code every other second or depending on your IP address.
We are investigating options to list progressive web apps that give the user more control of what is being run. While standard PWA manifests primarily contain metadata, a security-focused implementation could leverage several mechanisms to establish stronger integrity guarantees:
Extending manifest files with cryptographic commitments to all resources
Implementing Subresource Integrity (SRI) checks to verify each script matches expected hashes
Using a trust-on-first-use (TOFU) signature model where developer keys are stored after initial verification
Creating transparent, user-controlled update processes that display cryptographic verification before applying changes
Such an approach would significantly reduce trust requirements in the server after initial installation, as the PWA could verify the integrity of updates against developer signatures before execution. Static analysis could also differentiate between PWAs with secure update mechanisms versus those with silent automatic updates.
While not eliminating all risks, this model would provide a more verifiable path than traditional web wallets, potentially bringing them closer to the verification standards we apply to other wallet types.
[1] https://docsend.com/view/s/rmdi832mpt8u93s7
English speakers please help us out here ...
We are close to launching "attestations" where anybody will be able to attest to the reproducibility of binaries. The process is technical and quite involved. Are those who do this ...
* Attestators
* Wittnesses
* Verifiers
* Certifiers
#askNostr
Question for people who looked at individual reviews on  : Should we remove the individual coloring of pages based on the product's logo?
Please comment below or vote on Xitter
: Should we remove the individual coloring of pages based on the product's logo?
Please comment below or vote on Xitter 

WalletScrutiny
Know your wallet like you built it.
Not everyone is a developer. Not everyone has to be.

X (formerly Twitter)
WalletScrutiny (@WalletScrutiny) on X
Question for people who looked at individual reviews on https://t.co/np0b5LsMBI: Should we remove the individual coloring of pages based on the pro...
Today we welcome @npub1qw6s...4882 as our new lead developer! He brings a lot of experience not only with Bitcoin and nostr but even was involved with two reproducible wallet builds already years ago besides many other bitcoin tools he contributed to.